The role of a CISO leading the security team in a technology company demands continuous vigilance and a proactive response to a relentless tide of security threats and incidents. With security teams continuously searching for vulnerabilities, each day of threat management resembles an incident response crisis. During these processes, it is essential for CISOs and security teams to have a reliable risk monitoring and scoring mechanism or an industry standard that can assist in prioritizing and mitigating vulnerabilities with limited time and resources.
However, as the threat landscape evolves to present more complex and sophisticated threats, the traditional risk rating vulnerability managementindicators and protocols fail to process these threats accurately. Traditional vulnerability scoring is well-known to security teams and threat actors across the cybersecurity landscape. As a result, threat actors are increasingly focusing on exploiting vulnerabilities with relatively lower scores that can still have a high impact.
These changes call for a more advanced and reliable vulnerability management system that incorporates more factors in calculating risk/vulnerability scores, providing more accurate outputs for vulnerability management. This article highlights some of the existing challenges and discusses alternative solutions that address these challenges.
Current Trends and Challenges in Vulnerability Scoring
Consider a scenario where an organization’s security team has performed scans across hundreds of its applications, devices, and databases and unearthed thousands of vulnerabilities. Although the goal of fixing all these vulnerabilities is clear, the immediate problem lies in prioritizing these threats with limited resources and time.
The first instinct of any security practitioner is to rely on the industry standard, which dictates focusing on “High” and “Critical” vulnerabilities based on a risk/vulnerability score. Since 2005, CVSS (Common Vulnerability Scoring System) has been the guiding light for determining the score of vulnerabilities; however, lately, it tends to fall short of the requirements of the current threat landscape.
CVSS rates vulnerabilities on a scale from 0 to 10, with higher scores reflecting greater severity, and classifies them as Low, Medium, High, and Critical. While it is a straightforward system, in today’s complex threat landscape, it is akin to using a sundial to navigate modern-day oceans. Some of the prominent limitations of CVSS are listed as follows:
Growing Cyber Threats
In 2023, over 29,000 security vulnerabilities were reported worldwide (Petrosyan, 2024), which shows growth over the years. More than 57% of vulnerabilities in the National Vulnerability Database (NVD) are categorized as either “High” or “Critical” (National Institute of Standards and Technology., n.d.). This overwhelming number of critical alerts makes it increasingly difficult to discern genuine threats from less significant ones.
Limited Resources
According to studies, organizations address only about 10% of their open vulnerabilities each month (Baker, 2023). Additionally, nearly 60% of known exploited vulnerabilities remain unmitigated beyond their deadlines (BitSight, 2024).
Unreliable Metrics
One of the most sensational and impactful ransomware attacks, ‘WannaCry’ caused nearly billions of dollars in damages and had a seemingly lower CVSS score of 8.8. Meanwhile, other vulnerabilities with a perfect ten score on the CVSS metric haven’t been exploited to a similar degree (National Institute of Standards and Technology, 2024).
Quantity vs. Impact
Should the security team mitigate hundreds of vulnerabilities categorized as “High” or prioritize just a few categorized as “Critical”? This is a common dilemma in vulnerability management. What if a seemingly low-threat vulnerability combines with another to create a bigger problem? For example:
- Vulnerability 1: CVE-2017-8283 in Ubuntu VMs (10,000 instances)—This vulnerability might seem to have a critical impact due to the large number of affected assets. However, this vulnerability might not be exploitable if an organization hasn’t modified Ubuntu in their systems during setup. Mitigating it might lead security teams to a complex, potentially unnecessary workload.
- Vulnerability 2: CVE-2021-44228 (log4shell) in a Java-based web application (1 instance)—This might affect only one server, but if exploited, it can greatly impact the entire enterprise’s operations.
Consider the scenario of CVE-2017-8283 and CVE-2021-44228, where the former has a greater number of instances comparatively. However, it is advisable that rather than focusing on the number of affected assets, prioritizing vulnerabilities based on exploitability and potential impact is much more efficient. Thus, in this scenario, CVE-2021-44228 (log4shell) is a bigger threat, even though it affects fewer systems.
By understanding these nuances, security teams can make informed decisions about vulnerability management and avoid wasting resources on irrelevant mitigations. However, even this is time-consuming and still contributes to a high number of unaddressed known exploits. Even if an organization can successfully mitigate all the “High” and “Critical” vulnerabilities religiously, they must account for a fraction of known exploits remaining unaddressed. Thus, the CVSS scoring metric, which was once a guiding light for security teams, now seems like a flickering candle amid the storm of emerging vulnerabilities.
Advanced Metrics for Comprehensive Security Review
To address the above challenges, some new scoring systems have emerged as guides for the industry amidst growing threats from evolving attack vectors. Metrics such as Known Exploited Vulnerabilities (KEV), Exploit Prediction Scoring System (EPSS), and Stakeholder-Specific Vulnerability Categorization (SSVC) adopt real-time exploitation and compliant protocol approach to address some of the challenges posed by CVSS.
Known Exploited Vulnerabilities
CISA’s Known Exploited Vulnerabilities (KEV) is a database for intelligence on active vulnerabilities being actively exploited in real-world environments. Launched in November 2021, this initiative by the Department of Homeland Security of the U.S.A. aims to assist security teams and applications in securing networks against current and immediate threats. Hence, it is imperative to prioritize CVEs from this database for instant mitigation of imminent threats.
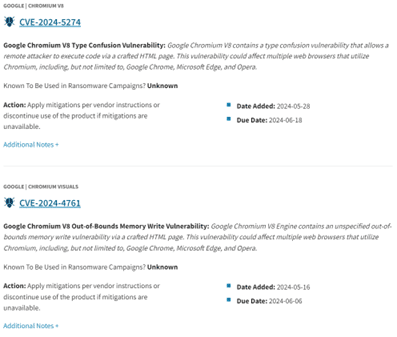
Source: (CISA, 2024)
Exploit Prediction Scoring System (EPSS)
This system servs as a predictive tool for an organization’s risk analysis capabilities, as it assesses real-world exploitation attempts and offers a more accurate perspective on possible exploitation of specific vulnerabilities. Introduced by FIRST in 2019, the EPSS (Exploit Prediction Scoring System) represents a groundbreaking approach by evaluating over 6 million observed exploitation attempts and incorporating data from multiple threat intelligence sources, CISA’s KEV catalog, and various vulnerability characteristics.
The results have been remarkable. Where the traditional approach of addressing all high and critical issues tends to overwhelm the security teams, EPSS on other hand, when incorporated into risk analysis with a reasonable threshold, significantly reduces the workload, easing the burden on staff. The EPSS score is based on the following factors (Shetty, 2023):
- Exploitation activity observed in the wild by reputable security vendors
- Publicly disclosed exploits, such as those listed in the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerability (KEV) catalog, Google’s Project Zero, and Trend Micro’s Zero Day Initiative (ZDI)
- Publicly accessible exploit code from sources like GitHub, Exploit-DB, and Metasploit
- Intelligence gathered from open-source security tools
- Mentions on social media
- References with specific labels
- Keyword descriptions of vulnerabilities
- Common Weakness Enumeration (CWE) identifiers
- Vendor-specific labels
- Age of the vulnerability
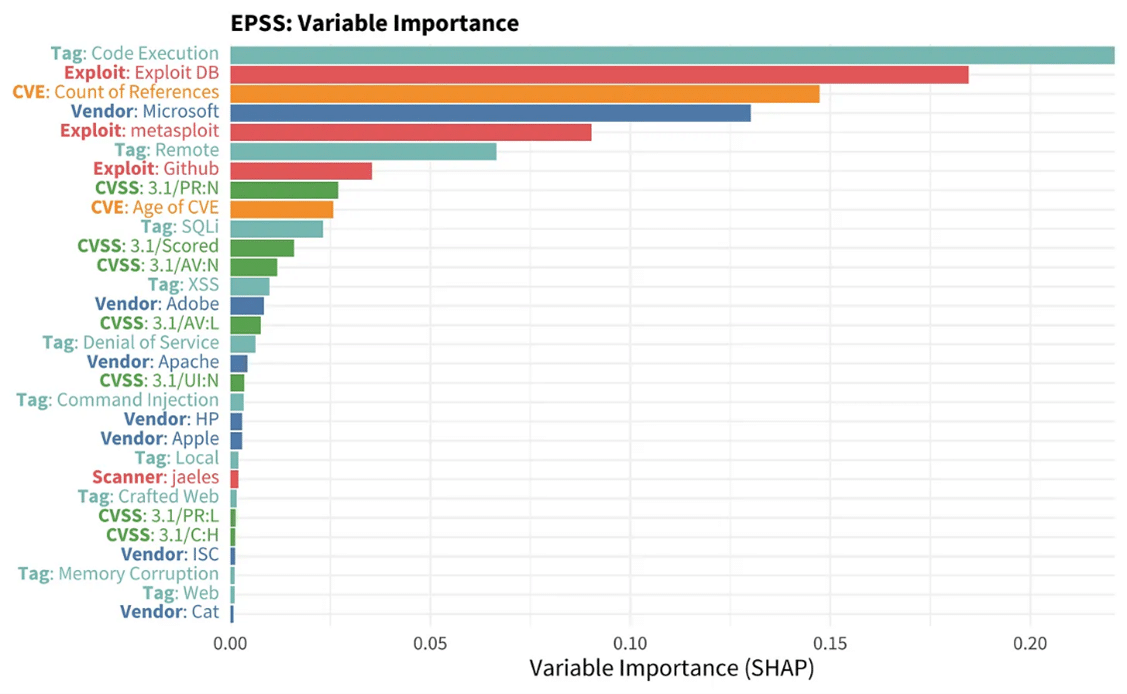
Figure:
The EPSS model has over 100 variables, and the figure provides the mean absolute contribution scores of the top 30 variables (Haydock, 2022).
The EPSS score, ranging from 0 to 1 for each published CVE, indicates the likelihood of exploitation within the next 30 days (Forum of Incident Response and Security Teams, n.d.). The score is updated daily as new data emerge.
The traditional approach of fixing all “High” and “Critical” vulnerabilities required security teams to mitigate a large volume of vulnerabilities in an inadequately prioritized approach. It would lead to fixing more than 80% of known vulnerabilities at the expense of great resources and time. However, in comparison, using the EPSS v3 with a threshold score of 0.01+, i.e., mitigating vulnerabilities scoring higher than 0.01, will allow organizations to achieve roughly the same outcome, while the amount of workload would have been reduced to resolving only ~2.7% of all known CVEs.
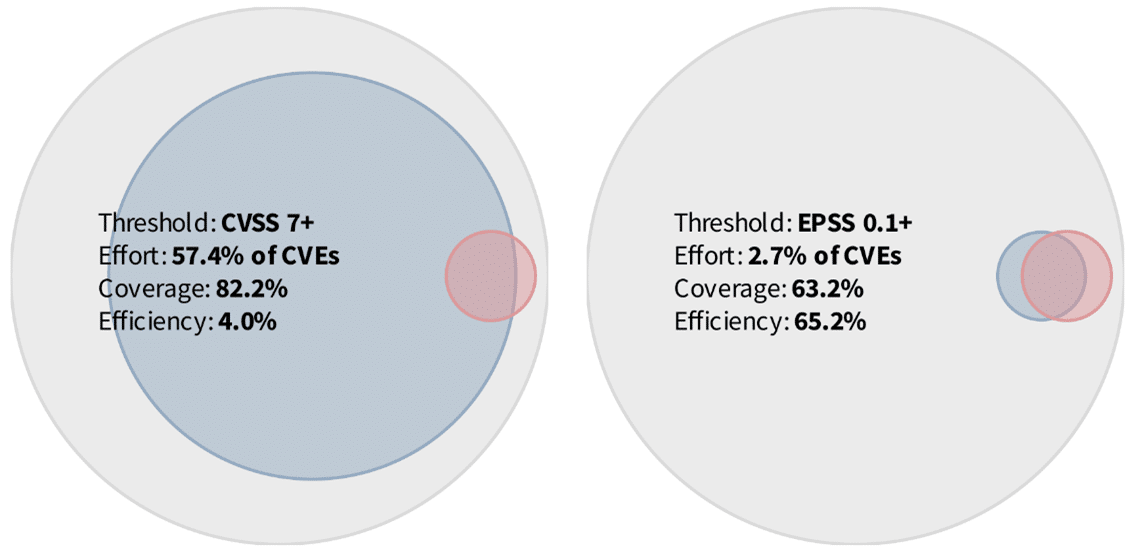
Source: (Forum of Incident Response and Security Teams, n.d.).
This approach requires only about 4.7% of the effort of that of the CVSS 7+ threshold (calculated as 2.7%/57.4%). By adopting this method, you could increase the efficiency of effort input by your overworked staff by 96.4% (100% – 4.7%), allowing them to better manage the numerous security tools and thousands of other security issues within your organization.
SSVC and the Future of Vulnerability Management Beyond EPSS
Despite the efficacy of Exploit Prediction Scoring System (EPSS) as a tool for vulnerability assessment, the process might not entirely consider the distinctive elements involved in an organization’s environment. Thus, a Stakeholder-Specific Vulnerability Categorization (SSVC) may provide the assessment with a more tailored approach.
Collaboratively developed by Carnegie Mellon University and CISA, the Exploit Prediction Scoring System (EPSS) utilizes a decision trees-based learning model to guide vulnerability analysis based on key factors such as exploitation status, impact, and prevalence (Shetty, 2024).
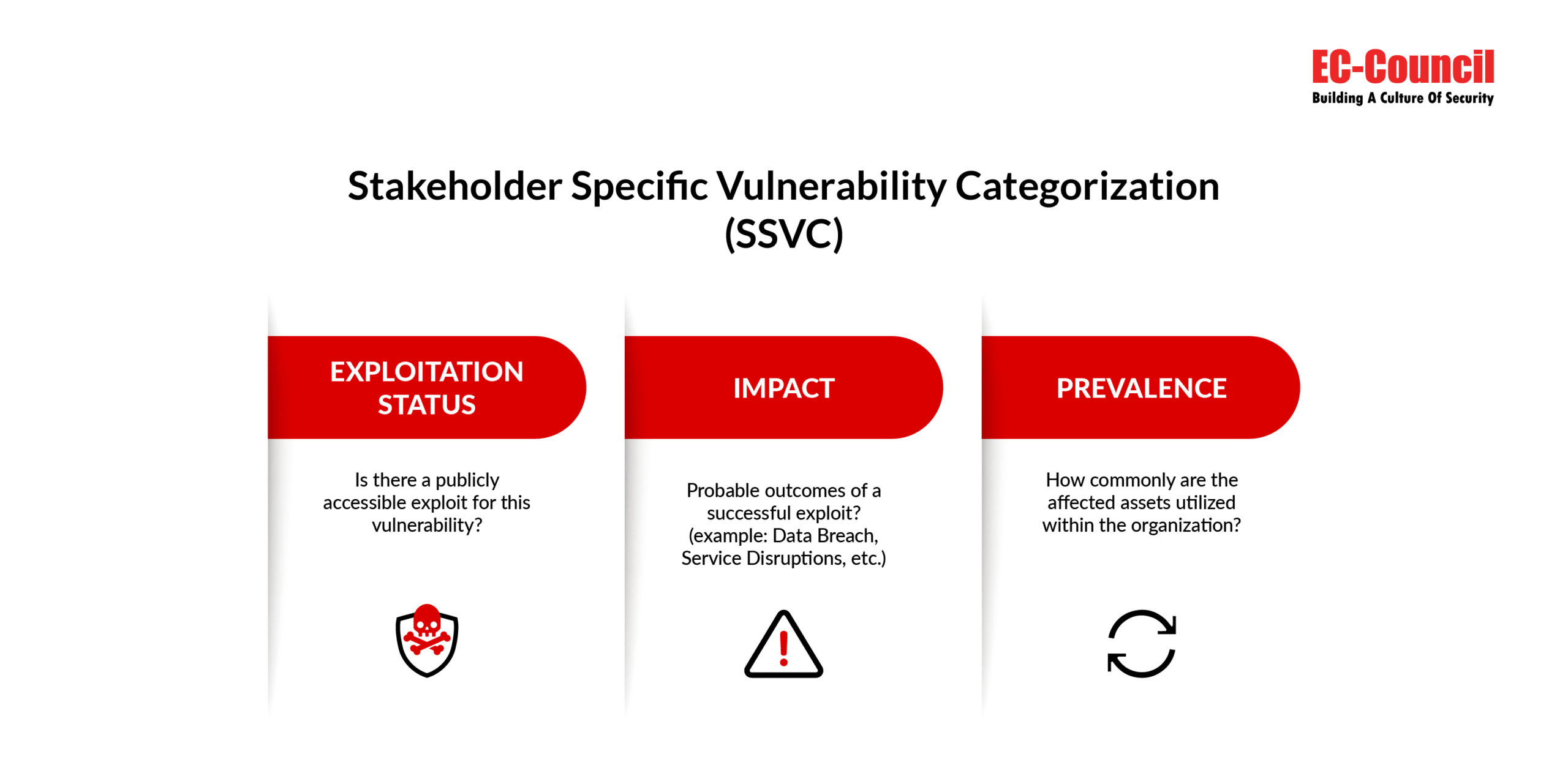
In order to make informed decisions based on the parameters suggested in the above image, security teams need to have a thorough understanding of vulnerability exploitation, its potential impact, and its prevalence within their organizations. The relevant expertise can be acquired through certification and training for vulnerability management.
Leveraging EC-Council Courses for Effective Vulnerability Management
EC-Council’s security education programs and certifications equip security aspirants with the technical skills to detect, identify, and understand vulnerabilities, as well as manage and mitigate them. The Certified Ethical Hacker (C|EH)also equips participants with skills to exploit vulnerabilities, allowing them to better assess exploitability and potential impact, whereas Certified Network Defender (C|ND)provides essential knowledge and understanding of the prevalence of vulnerabilities within a network. Along withCertified SOC Analyst (C|SA)Threat Intelligence Analyst (C|TIA), EC-Council’s certifications cover a broad range of security topics, including vulnerability management, risk management, and incident response, which equips aspirants with means to effectively assess, prioritize, and manage vulnerabilities.
Role of Security Leaders in Vulnerability Management
Security analysts and CISOs play a pivotal role in SSVC by leveraging the RACI (Responsible, Accountable, Consulted, Informed) matrix. Their leadership ensures that the organization makes informed decisions regarding prioritized vulnerability management and mitigation strategies.
The C|CISO program offered by the EC-Council provides crucial insights into the business aspects of information security. This broader understanding enables CISOs to effectively communicate security risks to senior management and advocate for the necessary resource allocation for vulnerability management.
By integrating SSVC practices with the expertise gained from EC-Council courses, security teams can move beyond a one-size-fits-all approach, and develop a robust, tailored strategy that meets their specific needs.
Reference
Baker, W. (2023, August 04). The Pithy P2P: 5 years of vulnerability remediation & exploitation research. Cyentia. https://www.cyentia.com/pithy-p2p/
BitSight. (2024, May 01). Bitsight Reveals More than 60 Percent of Known Exploited Vulnerabilities Remain Unmitigated Past Deadlines in First-of-its-Kind Analysis of CISA’s KEV Catalog. https://www.bitsight.com/press-releases/bitsight-reveals-more-60-percent-known-exploited-vulnerabilities-remain-unmitigated
CISA. (2024, July 25). Known Exploited Vulnerabilities Catalog. [Illustration]. https://www.cisa.gov/known-exploited-vulnerabilities-catalog
Forum of Incident Response and Security Teams. (n.d.). The EPSS Model. [Diagram]. https://www.first.org/epss/model
Haydock, W. (2022, February 28). Exploit Prediction Scoring System (EPSS): A deep dive [Graphs]. Stackaware. https://blog.stackaware.com/p/deep-dive-into-the-epss
National Institute of Standards and Technology. (n.d.). National Vulnerability Database. https://nvd.nist.gov/general/nvd-dashboard
National Institute of Standards and Technology. (2024, May 29). CVE-2017-0145 Detail. https://nvd.nist.gov/vuln/detail/cve-2017-0145
Petrosyan, A. (2024, August 20). Common IT vulnerabilities and exposures worldwide 2009-2024. Statista. https://www.statista.com/statistics/500755/worldwide-common-vulnerabilities-and-exposures/
Shetty, V. (2023, October 23). CISO’s Dilemma: Why Focusing on High and Critical CVSS Is an Inefficient Effort for their team. Varindia. https://www.varindia.com/news/cisos-dilemma-why-focusing-on-high-and-critical-cvss-is-an-inefficient-effort-for-their-team
Shetty, V. (2024, January 17). Beyond Vulnerable: Understanding the Nuances of Exploitability in Vulnerability Management. LinkedIn. https://www.linkedin.com/pulse/beyond-vulnerable-understanding-nuances-exploitability-vinyl-s-16ifc/
Tags
About the Author











