VAPT Career Path
Vulnerability Assessment and Penetration Testing
Attain World's No.1 Ethical Hacking Certification with Comprehensive Network Security Skills and Advance Penetration Capabilities!
Become a Vulnerability Assessment Specialist
"*" indicates required fields
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






VAPT Career Path
Vulnerability Assessment and Penetration Testing
Attain World's No.1 Ethical Hacking Certification with Comprehensive Network Security Skills and Advance Penetration Capabilities!
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






Become a Vulnerability Assessment Specialist
"*" indicates required fields
Vulnerability assessment and penetration testing (VAPT) is a technique to protect an organization against external and internal threats by identifying security threats. VAPT professionals can secure the organization’s network infrastructure, web application, and mobile application security assessment to detect and gauge security vulnerabilities with ethical hacking, network security, and penetration testing skills.

Your Pathway to a Vulnerability Assessment and Penetration Testing Career
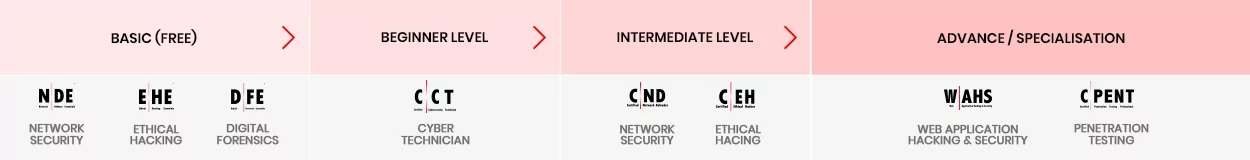
A novice should begin their journey by building a solid foundation in the core areas of cybersecurity. Start by getting the basics right with the Network Defense, Digital Forensics, and Ethical Hacking certification; the course to prepare for this certification is completely free.
Attain a basic core certification of the Certified Cybersecurity Technician (C|CT) to begin your professional cybersecurity course. C|CT will immerse students into well-constructed knowledge transfer through training, accompanied by critical thinking challenges and immersive, hands-on lab experiences allowing candidates to apply their knowledge and move into the phase of skill development right in the class.
Post C|CT, you need to grow your career path with the Certified Network Defender certification. You will learn to examine network traffic at the binary level, master TCP/IP protocol, introduce vulnerability assessments and hacking methodology, and much more. These are essential skills that a VAPT professional should possess, a good foundation to become a network security expert.
Once you have a solid foundation, you will be ready to move into ethical hacking with Certified Ethical Hacker (C|EH) course, Worlds No.1 Ethical hacking certification. C|EH learning framework Learn, Certify, Engage and Compete framework covers a comprehensive training program to prepare you for the certification exam and the industry’s most robust, in-depth, hands-on lab experience of any cybersecurity program available. The C|EH certification will help you get into the Hackers mindset and expose you to the 5 phases of ethical hacking, which will allow you to acquire the skills to become a competent professional in the vulnerability and penetration testing world.
Post C|EH, we recommend you take up Web Application Hacking and Security, a specialization certification that enables you to play, learn, hack, test, and secure web applications from existing and emerging security threats in the industry verticals.
After mastering the 5 Phases of Ethical Hacking, you will be ready for penetrating testing. With the Certified Penetration testing Professional course will learn advanced penetration testing skills such as Advanced Windows Attacks, Internet of Things (IoT) Penetration Testing, Penetration Testing in OT and ICS/SCADA Environments, Exploit Writing and Advanced Binary Exploitation, Bypassing Filtered Networks, Accessing Hidden Networks with Pivoting and Double Pivoting, Privilege Escalation, Defense Evasion, Attack Automation with Scripts and many more.
Learn to Strengthen the Security Posture, By Identifying Vulnerabilities That Adversaries Can Exploit.
CPENT = HACKING WITH A PURPOSE!
Job Roles Mapped to Vulnerability Assessment and
Penetration Testing Career
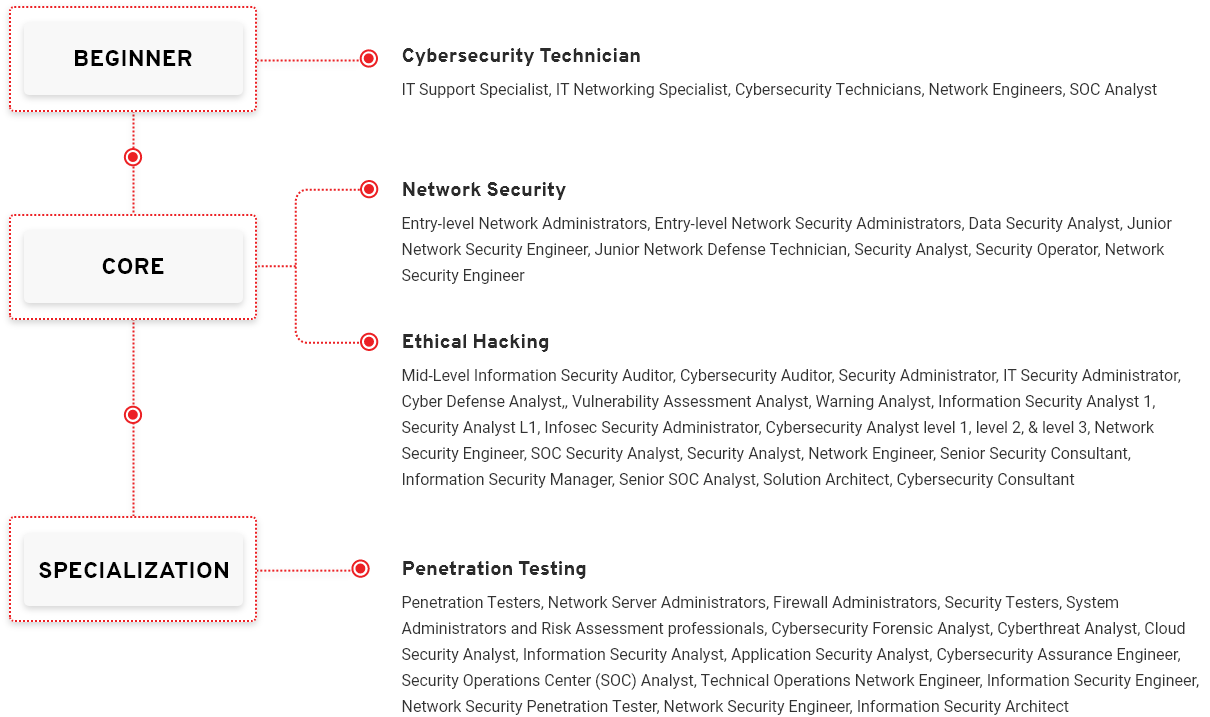
Job Roles Mapped to Application Security Career Path
7 Reasons to choose Vulnerability Assessment and
Penetration Testing Career
- Growing Industry : Considering the recent hacks across the globe, it has become imperative for companies to keep their information and business secure, for which they need a formidable team of cybersecurity professionals skilled, especially in VAPT, to perform various monitoring, testing, and securing tasks.
- Job Vacancies : Apply for Different Job Roles mapped to VAPT Career Path. With almost 3 million job vacancies globally, cybersecurity is an attractive industry.
- Rewarding : The salary of a Certified Ethical Hacker is $105,031 (as per salary.com), and that's just the beginning of your career.
- Begin and Build Your Rewarding Cybersecurity Career with World's No.1 and Highly Sought Cybersecurity Credentials.
- Accreditations : C|EH and C|ND courses are ANSI Accredited, and DoD (US. Department of Defense) Approved.
- Expert, Experienced Trainers & SMEs: Career path courses are developed and taught by EC-Council with 20 years of experience in cybersecurity training, industry experts, and professionals along with professional instructors with years of cybersecurity experience.
- Lab intensive courses to develop real world job skills.
How does VAPT help the organization
VAPT FAQs
A Vulnerability Assessment and Penetration Testing (VAPT) certificate is a valuable credential that substantiates a candidate’s skills in testing and patching security vulnerabilities found in an organization’s applications and IT network to protect it proactively from internal and external security threats.
A penetration testing process is divided into five stages: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Learn about each of the five phases of the penetration testing process in greater detail in this article.
VAPT stands for Vulnerability Assessment and Penetration Testing. This process helps organizations identify and fix security weaknesses before attackers can exploit them. VAPT also helps organizations meet regulatory compliance requirements and protect their reputations.
The global market for VAPT is expected to grow at a rate of 7.5% from 13.34 billion USD in 2019 to 23.56 billion USD in 2027.1 Such growth suggests an increasing job demand. An average of approximately 19,500 openings per year for information security analysts are anticipated over the next decade.2
Vulnerability assessment involves utilizing specific tools to identify, categorize, and evaluate vulnerabilities present within a system. On the other hand, penetration testing involves actively exploiting vulnerabilities to assess their severity, authenticity, potential for harm, and other related information.
When conducting VAPT, there are essential guidelines and protocols to ensure that the testing is thorough and reliable. Some of these best practices include the following:
- A certified and experienced professional should conduct the test.
- Define the scope and objectives clearly before the start of testing.
- Use the latest testing tools and techniques.
- Conduct comprehensive testing of all systems, networks, and applications.
- Prepare a thorough report that includes findings and recommendations after the testing process is complete.
VAPT can be used to improve overall security posture by identifying vulnerabilities and providing recommendations for remediation. This allows businesses to address weaknesses in their security infrastructure, leading to a more robust and secure environment.
Here is the list of best VAPT tools that are commonly used by professional pen testers:
- Metasploit
- Nmap
- OWASP Zap
- Burp Suite
- Wireshark
- Intruder
- sqlmap
- w3af
- Acunetix
Accreditations, Recognitions & Endorsements













